Phantom Tap (PhanTap) - An ‘Invisible’ Network Tap Aimed at Red Teams. With limited physical access to a target building, this tap... Read more »
Phantom Tap (PhanTap) - An ‘Invisible’ Network Tap


Phantom Tap (PhanTap) - An ‘Invisible’ Network Tap Aimed at Red Teams. With limited physical access to a target building, this tap... Read more »

TOR Router- A tool that allow you to make TOR your default gateway and send all internet connections under TOR (as transparent proxy) fo... Read more »

Use Top Secure VPN For Online Privacy Your Internet data is selling without your permission. Last week US President Donald Trump has ... Read more »

MongoDB-HoneyProxy: A Honeypot Proxy For MongoDB Server When run, this will proxy and log all traffic to a dummy mongodb server. MongoD... Read more »

Paros: A Java - Based Web Proxy Tool Paros is a Java based HTTP/HTTPS proxy for assessing the vulnerability of web application. An... Read more »

Inexpensive Webcams Easily Turned Into A Network Backdoor According to the researchers, we can easily turn webcam connected device... Read more »

Whonix - Privacy Protection And Anonymity Operating System Whonix is a free and open-source desktop operating system (OS) that is sp... Read more »

Toxy: Hackable HTTP Proxy To Simulate Server Failure Scenarios And Unexpected Network Conditions toxy is a fully programmatic and hack... Read more »

Inveigh: A Windows PowerShell LLMNR/NBNS Spoofer With Challenge/Response Capture Over HTTP/SMB. Inveigh is a Windows PowerShell L... Read more »

Kunai 0.2 Pwning And Info Gathering via User Browser. Sometimes there is a need to obtain ip address of specific person or perform cli... Read more »

Ricochet 1.1.0 - TOR Secure Peer-To-Peer Client Ricochet is an experiment with a different kind of instant messaging that *doesn't... Read more »

Nuke-IOS An Auditing Tool To Test ARP Attacks For iOS. Its an auditing tool to test ARP attacks, can easily be avoided using Static-AR... Read more »
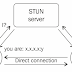
Get Original IP Address Of Any User From STUN IP Address Requests For WebRTC Firefox and Chrome have implemented WebRTC that allow requ... Read more »

How To Configure Tor and Privoxy Using Proxy Chains In Kali Linux as Anonymous way ? Follows to use tor as a proxy in order to use the ... Read more »
Ghost Phisher is a Wireless and Ethernet security testing tool written in Python Programming Language and the Python Qt GUI library. ... Read more »
![How To Install Tor - Polipo Proxy With SQLMap [#Video]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjILdE2q7xofCWhkd11-9Uawzh4S3W2ZMGTSMFzFeaQ-ZhHegd_H0caZlS8k0wOh9WcIgxoQ8kV7mpEe4gCQwGg_T1g2ZFjRL9GUXN41UDwJxAcY0-Oub0VnY8MEaFuiviV48JF8U-bC7gW/s72-c/Security.jpg)
How to install Tor - Polipo Proxy With SQLMap? Commands: Install tor + polipo and then back up # apt-get install tor tor-geoipd... Read more »